THM: Blog Room Writeup
Here is the link of this great room: Blog by Nameless0ne.
Let's start guys..
Enumeration
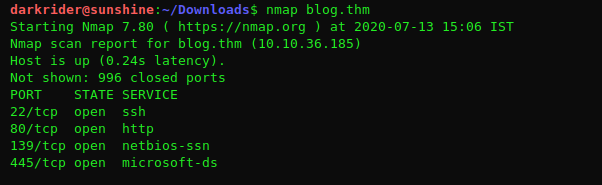
First I ran the nmap scan:
1.First lets check out the Blog itself running on the port 80. From little enumeration we can say that this is a simple blog running on the Wordpress.
2. The blog contains a single post by a user named Karen Wheeler for Billy joel.
3. To enumerate the users on the blog I will be using WPscan.
wpscan --url blog.thm -e u
This command will list all the users on the Blog, bjoel & kwheel.
4. Let's try to find out the password of these users using the same tool again.
wpscan -U username --password <pass file> -t 30 --password-attack wp-login --url blog.thm
5. Try to run your own command. It won't take long before the password pops. (hint: try Mom name)
6. After login into the wordpress I saw the user had very limited capabilities so there must be some other way to the shell or some kind of RCE!!
7. Lil bit enumeration showed us that the wordpress is using version 5.0 which is vulnerable to Remote code execution vulnerabilty via Crop-image functionality.
8. So let's get the exploit in our computer and start hacking.
But before that let's enumerate our SMB service too ;) ( I won't take long)
smbclient -L blog.thm -U Anonymous
After that I used smbclient \\\\blog.thm\billySMB -U Anonymous
I downloaded all these files to my machine, analyzed them using Steghide, binwalk and exiftool and you know what this is a rabbit hole!
9. Back to our exploit. Fire up Metasploit(don't forget, always keep them updated)
10. Fill up all the options, also set the username and password which you got from the previous WPscan attack.
11. This will give us a nice Meterpreter shell. Enter 'shell' in the Meterpreter command line and then start enumerating the machine.
Privilege Escalation
12. So our first flag user.txt is not at its usual location /home/bjoel/user.txt. Then I tried using the find command but no success.
13. After some enumeration I find out there is a unusual suid binary lying out there..
find / -perm -4000 2>/dev/null
14. The binary which stands out is Checker.
15. So I downloaded the binary and reversed it using Radare.
> r2 -AAAA checker
> pdf @main
For simplicity I am adding the C source code which I got from Ghidra.
{
char *pcVar1;
pcVar1 = getenv("admin");
if (pcVar1 == (char *)0x0) {
puts("Not an Admin");
}
else {
setuid(0);
system("/bin/bash");
}
return 0;
}
So what this function is doing is that it is calling getenv( ) on admin and returning its value which is obviously null, because the environment variable named 'admin' does not exist.. right?
So if we add an environment variable and set its value to not null then we could execute our 'else' part of the code..which is calling the Bash as root.. simple.
> export admin = '1'
This command creates a new variable with the value 1. And now we run the checker binary..
And you got the root.
Capturing Flags
1. Root flag is at its normal place.
2. For user flag
And this is it. :)
Thankyou for reading it.
- DarkRider88








Nhaeri0tina Cody Bou https://wakelet.com/wake/DxHkpqQw7bXbSmoZdNjUW
ReplyDeletesteatlomolin