Blunder Writeup | HackTheBox | By Valerie23
Gathering information
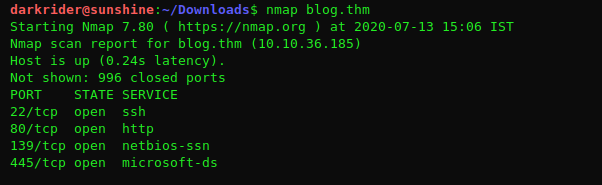
Let’s start with a nmap scan to establish the open ports in the host.
Website Analysis
Now we should start enumerating port 80. So lets check out the source code of the homepage and see if we are able to find any additional clues.
We found this /about directory
There doesn't seem to be anything useful in this directory.
Lets fireup a GoBuster scan
gobuster dir -u http://10.10.10.191 -w /usr/share/wordlists/dirb/common.txt -t 50
The /admin directory looks like:
Now we have a login panel, all we need is a username and a password.
GoBuster extension
Its always good to perform some further enumeration of the webapp using custom file extensions to find out any hidden backup files or some notes :)
$ gobuster dir -u http://10.10.10.191 -w /usr/share/wordlists/dirb/common.txt -x txt,zip -t 50
Using the -x flag to look for some specific extensions such as txt,zip we get a /todo.txt file.
Here we can find a username "fergus".
Now is the time to start looking for password.
CEWL
Cewl is a ruby based command line tool which spiders a given url to a specified depth, optionally following external links, and returns a list of possible passwords.
Lets create our own wordlist using using the command below:
$ cewl --with-numbers -w cewlwordlist -d 5 http://10.10.10.191/
Before bruteforcing the login page lets expand our knowledge bit more about BLUDIT CMS ,its vulnerabilties, exploits etc.
In the process of doing so we came across this article that reveals that we cannot bruteforce the CMS(obviously) since it will block our IP after a specific number of requests. So we will use a script that will use "X-Forwarded-For" header for sending different values in place of our IP.
Read the article for detailed explanation.
The article also provides us the github link for the script...good ( I am too lazy to write my own script, hahah)
Let's clone the script from github to our local macine and run it:
$ python3 bruteforce.py 10.10.10.191 fergus cewlwordlist
we get the following result:
Lets take the help of google again and look for possible exploits:
Our search helped us find information about "Bludit Directory Traversal Image File Upload Vulnerability" which has a public metasploit exploit ( again cool).
Its time to start metasploit:
(ALL, !root) /bin/bash (CVE-2019-14287) means that user hugo cannot run /bin/bash as root, but this does not mean that he cannot run bash as any other user.
Since Sudo doesn't check for the existence of the specified user id and executes the command with arbitrary user id with sudo privileges.
And... we got our first shell.
Getting user flag:
While traversing around the directories looking for something interesting we can find this folder...
/var/www/bludit-3.9.2/bl-content/databases
it contains a file named users.php, lets take a look at its content
Voila! We found another password hash
We can now copy the hash & salt of admin into our terminal and determine its type using hash-identifier.
$ hash-identifier bfcc887f62e36ea019e3295aafb8a3885966e265
Using hashcat for cracking the password, we get, Password120 as the cracked password. Moving to the /home directory we can find two users named hugo and shaun.
Since hugo's directory contains user flag we try the password to escalate our privileges from www-data to hugo.
$ su hugo
Now we can read the user flag.
PRIVILEGE ESCALATION
Now that we have found our user flag the next thing that we need to do is try and find a way to escalate our privileges from hugo to root.
Since we have hugo's password we do our standard enumeration and do
sudo -l
And here's how the result looks like:
Since Sudo doesn't check for the existence of the specified user id and executes the command with arbitrary user id with sudo privileges.
sudo -u#-1 /bin/bash
-u#-1 in the above command returns as 0 which is root's id and /bin/bash is executed with root's permission and as a result we get root privileges.
Now we can read the root flag located in the /root directory.
-by Valerie23









Comments
Post a Comment