Unbalanced writeup | HackTheBox | by Darkrider88
Enumeration:
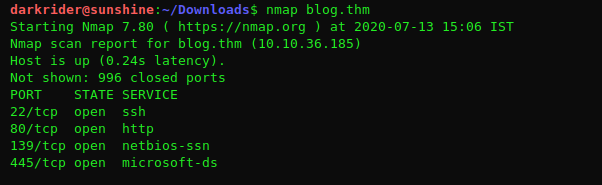
Nmap scan:
There is an interesting port 873 running rsync.
Rsync enumeration:
Rsync is a most commonly used command for copying and synchronizing files and directories remotely as well as locally in Linux/Unix systems.
First I will try to list the files or folders inside it and dump all the files.
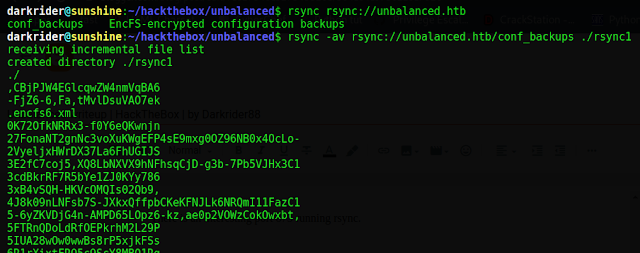
rsync -av rsync://unbalanced.htb/conf_bakcups ./rsync
There is an .encfs6.xml file in this folder which tells that encfs utility is used to encrypt all the files and folders.
Let us decrypt all the files
John:
There is script in john to extract the hash from .encfs6.xml.
Cracking the .encfs6.xml file
$ locate ecnfs2john
$ sudo /usr/share/john/encfs2john.py ./rsync/ > encfs_hash
$ sudo john -wordlist=/usr/share/wordlists/rockyou.txt encfs_hash
Decrypt the rsync files and copy to other folder:
$ encfs ~/hackthebox/unbalanced/rsync/ ~/hackthebox/unbalanced/rsync_decrypted/
And now we have a list of files.
I checked all the files but the real juice was in the squid.conf and that was quite obvious. So there I found a password and a new domain intranet.unbalanced.htb and some keywords like cache_mgr. So I searched for all of this and found a tool called Squidclient which could be used to access the proxy server or cache.
Squidclient:
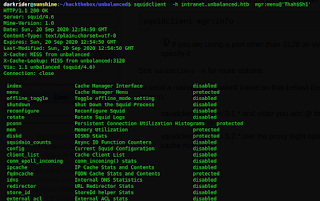
$ squidclient -h intranet.unbalanced.htb -w 'Thah$Sh1' mgr:menu
output:
So I got the list of indices and I started to enumerate them one by one. just replace mgr:index
and remaining command will be the same. The one index which stood out was fqdncache.
On enumerating it I got
I tried to access these domains but ofcourse they were not accessible because they are running on different IPs, but as we know Squid is a proxy and we need to access these domains with our proxy.
Enumerating sub domains:
Now add unbalanced.htb:3128 to foxy proxy, you can also add manually in the browser.
Then I tried to access these domain, remember to access all of these and enter their IP only.. and on all 3 IPs I got the same page.
Only one of them was valid for me it was 172.31.179.1
Enter something in the form and you will be presented with the message Invalid Credentials.
After testing a bit and asking for hints I got to know that there is a XPATH Injection in the form.
XPATH Injection testing
Reference: https://book.hacktricks.xyz/pentesting-web/xpath-injection
In the username field enter(with quotes): ' or true() or '
This will output all the usernames in systems. And we will do the same for extracting passwords.
I have made a script for this
Run the above script after getting all the usernames(change the usernames accordingly in the script)
User Flag:
So 'bryan' is our potential user and login with SSH. Grab the user flag and read TODO file.
The pi-hole service is running on port 8080 and I used ssh to forward this port on my local machine.
$ ssh -L 8080:localhost:8080 bryan@unbalanced
Opened it from a browser and tried most basic password 'admin' and I was in. Now I checked its version and found out public exploits. And there were quite a lot. I used this one https://github.com/team0se7en/CVE-2020-8816
I downloaded the binary and ran the exploit.
I got the reverse shell as www-data of docker container and after that little bit of enumeration and there was cleart text password in /root.
There is nothing much now.
- by DarkRider88







Comments
Post a Comment